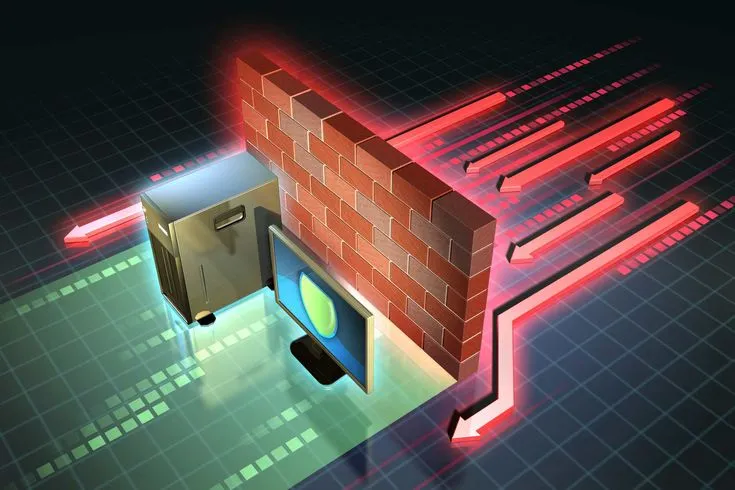
Firewall
Firewalls are crucial network security devices that monitor and control incoming and outgoing network traffic based on predetermined security rules. They act as barriers between trusted internal networks (like LANs) and untrusted external networks (like the internet), preventing unauthorized access while allowing legitimate communication.
Modern firewalls employ various techniques such as packet filtering, stateful inspection, and application layer filtering to enforce security policies effectively. They are essential in protecting against unauthorized access, malware, and other cyber threats by inspecting data packets and determining whether to allow or block them based on predefined rules.

 Consistent Speeds
Consistent Speeds Uninterrupted Service
Uninterrupted Service
 Proactive Monitoring
Proactive Monitoring Immediate Issue Resolution
Immediate Issue Resolution
Additionally, firewalls can provide logging and reporting capabilities, aiding in network visibility and incident response. Deployed at network boundaries or on individual devices, firewalls play a critical role in maintaining the integrity, confidentiality, and availability of network resources in today's interconnected digital environments.
